
When thinking of creating our second computational photography artifact, we were particularly interested in image steganography, the process of hiding information within an image. Moving with this idea, our final project encodes a file of user choice within an image undetectable to the eye, then extracts the message to be displayed back to the user as read. All photos used were either created by or taken by ourselves.


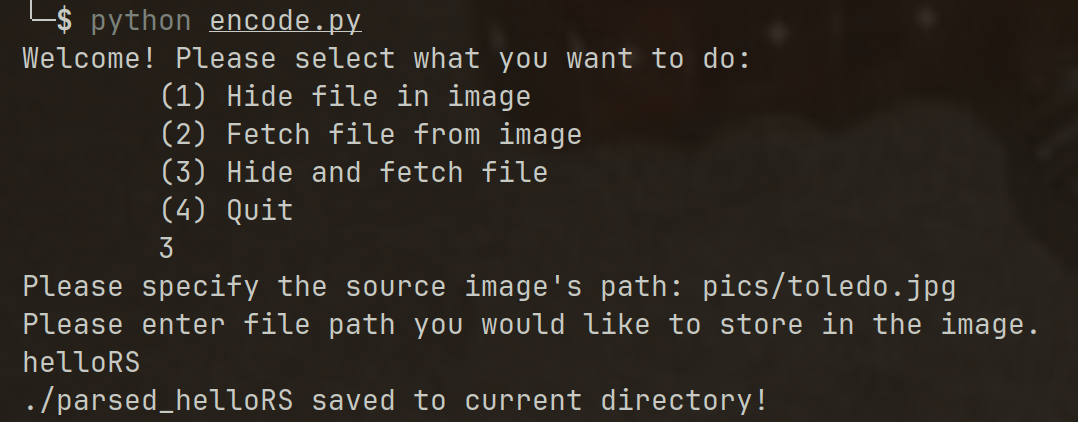


Comparing the original image with the modified one, it is clear the sky has a different shade of blue, indicating something is wrong; however, if presented only with the modified image, it is hard to tell the image has a hidden executable within it. This example did not encrypt the binary before hiding it in the image, meaning it is easy to create a program that can detect it, but encryption would avoid this possibility. In terms of real world use, this presents how malware can evade detection by antivirus software by embedding itself in images that appear benign.
Designed by Caleb Jones, Thomas Dean, Annarose Hilhorst, and Noah Flanagan
Return to the CS 4475 webpage